By Bharat Kapoor, Vice President of Online Brand Protection, Authentix
With online sales continuing to surge, companies are focusing on digital marketing and advertising products through various social media channels.
Not only has there been a rapid shift towards sales through online channels as a result of Covid-19, with corporations such as L’Oréal for example reporting a 62% increase in online sales across divisions and regions, the marketing of products through influencers has also experienced a dramatic uptick with the influencer marketing industry estimated to be worth US$9.7bn in 2020.
However, according to a report published by Instagram, 20% of the posts associated with top brands on social media featured counterfeit or illicit content.
The way customers interact with brands has been changing over time with two factors driving that change. One is technology where you have omnichannel sales and you’re getting messaging from social media feeds, e-commerce, marketplaces, influencers and so on. Customers buying products online also have access to delivery infrastructures that haven’t before existed in the way they do today. For example, if you buy something on Amazon in Southeast Asia, Asia or the US, it can come to you within hours. And what counterfeiters really take advantage of is exactly that: they find places where it’s easy for them to promote and sell anonymously and use this delivery infrastructure that’s been created by other legitimate businesses who have invested billions and billions of dollars in e-commerce.
The second thing that is helping smooth the path for piracy are payment systems that make it possible to move funds cross-border seamlessly, which are often associated with e-commerce and the rise of China’s cross-border ‘daigou’ trade. Via this method, counterfeiters will attempt to use the pricing gap between retail prices and grey market products to sell counterfeits.
Today, with the various means of transacting, getting money from someplace in Europe into China is also instant. This type of financial structure unfortunately is geared up to benefit fraudsters.
What we’ve seen is cross-border e-commerce channels becoming extremely popular because they offer crazy discounts. These deals are backed by sellers in a foreign country that will be responsible for delivering the product once a transaction is completed. For example, we found and investigated sellers in Singapore that have no inventory and they simply place a back-to-back order when they receive an order. This makes it more complicated for the police to take criminal actions against such sellers.
For the cosmetics industry for example from a brand perspective, it’s not only about counterfeiting, which may be 30-40% of the issue. But you will also find infringers using other brand assets – films, photos, design patents, a wide spectrum of IP – to sell a particular product that could be a counterfeit, or even a lookalike product.”
Finding Out Who’s Selling Fakes
SIPI has a unique strategy for discovering the online vendors who are responsible for dealing in counterfeit products and those dealing in legitimate goods via its proprietary online monitoring and enforcement solutions. The aim is not only to protect clients’ brand image and copyright, but also their customers and reputation.
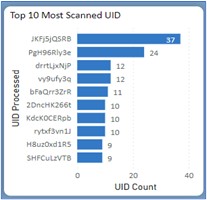
SIPI uses machine learning-based algorithms to scale up analysis and identify hidden trends in data gathered both online and offline to identify high-value targets.
The process begins with data gathering, in which SIPI scrapes data for clients’ brands from around 500 different e-commerce marketplaces and social media platforms. This data is fed into its online platform for risk screening and risk-scored by SIPI’s proprietary algorithms, under which over 30 parameters (including price, images, keywords, customer reviews and seller activity) are taken into account.
In terms of the algorithms, you must approach your research and your study of a potential infringinglisting by looking at the listing in the wider context. It is sometimes quite difficult to identify a counterfeit product just by looking at the listing, because legitimate brand owners may also sell their products at discounted prices. They have other channels and many other ways of selling. So, you can’t just say that the price of a product being 30% or 40% below average is, alone, an indication of it being counterfeit.
You must be more diligent in terms of your assessment of a seller. And that’s what SIPI has trained our algorithms to do – to know what else to look at online. For example, you can look at customer comments, store rating, how old the stores are and the types of products that you see the store selling, such as luxury goods alongside very generic products, which may be viewed as being suspicious.
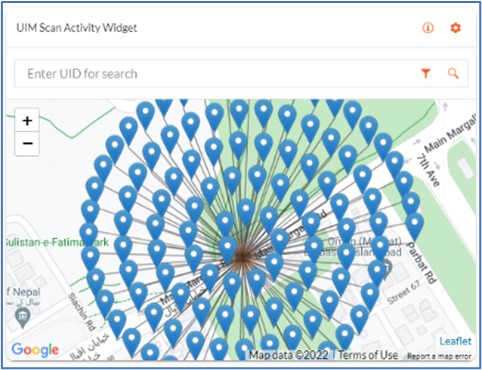
To identify offline targets, high-risk sellers are further investigated to create seller and product clusters, the name for groups of sellers concentrated in a region or dealing in a single product. A complete digital profile is created for high-value targets after which these leads are shared with an offline investigator for further investigation and action. The remaining infringing listings are reported to the respective marketplaces and social media platforms for takedowns.
SIPI currently protects over 200 brands and maintains a 94% success rate across platforms. While it strives to have a 100% success rate, certain major marketplaces in China and Asia make it extremely difficult to file complaints against each and every counterfeit instance.
And it is not simply a case of either how sophisticated or poorly-made the fake products are as to whether these are blatantly obvious versions. There are multiple avenues for illicit commercial activity.
SIPI has noticed a sharp increase in the number of sellers claiming to manufacture products and supply packaging materials that support the counterfeiting trade. There are also cases of verifiable and legitimate products being sold illegally.
Looking Forward
Given the wider e-commerce environment playing so well into counterfeit sellers’ hands, we believe the combination of Authentix and SIPI’s expertise comes at a beneficial time for brand clients. The acquisition of SIPI by Authentix increases the scope of its offerings to brand protection clients by integrating digital security technologies and online anticounterfeiting and content rights services for an end-to-end, comprehensive brand protection solution.
SIPI provides clients with solutions to digitize their supply chains and uses investigation techniques to determine instances of counterfeiting and diversion while attempting to keep the internet free of fakes by building effective online enforcement programs.
For a limited time, SIPI is offering a free online brand risk analysis to qualified brands. More information can be found here.

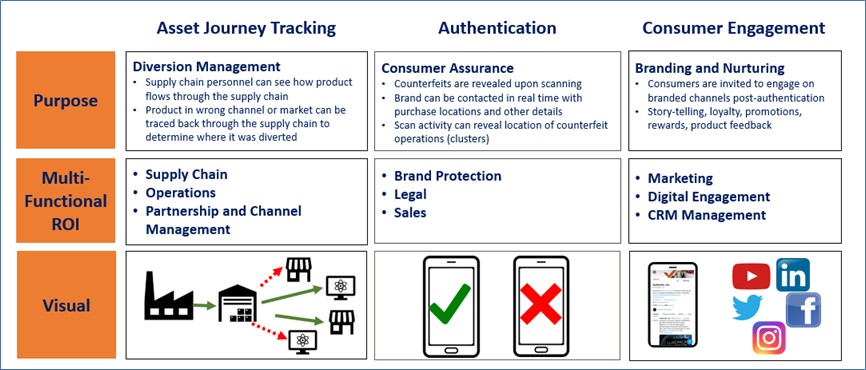






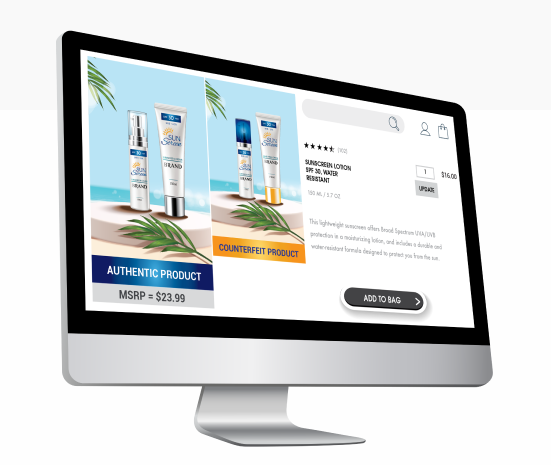
 To expand its capabilities in digital brand protection for brand owners, Authentix has recently acquired Strategic IP Information Pte Ltd (SIPI), a leading online brand and content rights protection service.
To expand its capabilities in digital brand protection for brand owners, Authentix has recently acquired Strategic IP Information Pte Ltd (SIPI), a leading online brand and content rights protection service.
 Authentix is pleased to be included in the June/July edition of
Authentix is pleased to be included in the June/July edition of 
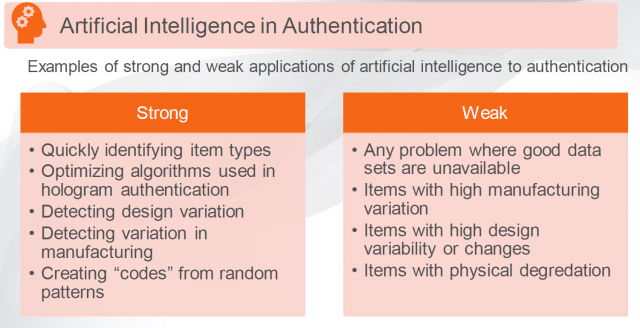
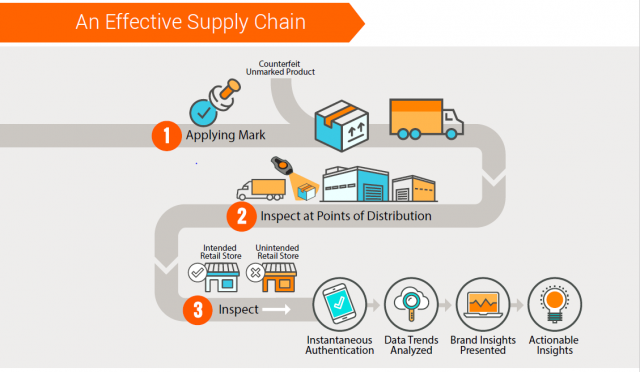
 The current counterfeit landscape is a “not if, but when” environment. At some point, brand owners will experience an unauthorized product in their supply chain. Given this inevitability, your product security strategy should be thorough, with a strong emphasis on implementation planning to enable detection of problems and action to mitigate and manage accordingly. One of the most effective deterrents to risk is teaming with a partner with the requisite skills, experience and talent to assist you in all facets of brand protection.
The current counterfeit landscape is a “not if, but when” environment. At some point, brand owners will experience an unauthorized product in their supply chain. Given this inevitability, your product security strategy should be thorough, with a strong emphasis on implementation planning to enable detection of problems and action to mitigate and manage accordingly. One of the most effective deterrents to risk is teaming with a partner with the requisite skills, experience and talent to assist you in all facets of brand protection.