By the Authentix Brand Protection Team
Whether you’re a brand owner protecting a commercial product or a government authority issuing critical, high-security documents, you’re continually faced with the ongoing challenges of combating illicit trade and counterfeiters.
To counter these constant attacks on legitimate industry players, high security authentication solutions are needed to safeguard the integrity of global commerce and can include both physical and digital security solutions. Security can be added to documents, products, and product packaging or labels. In addition to adding these security features, the more advanced and effective authentication programs should also include track and trace capabilities that allow the tracking of protected products throughout the supply chain.
With a comprehensive and well-curated authentication program, brand owners and governments can take a more proactive approach to protecting consumers from potential health and safety issues and themselves from the financial impacts of counterfeiting and diversion.
Product Marking: The Foundation
Physical marking solutions can range from simple yet effective to highly sophisticated and extremely secure. A typical marking ‘toolkit’ consists of four basic elements, each of which performs a different function, ranging from detection, prevention, deterrence and engagement.
- Tamper Evident – cannot be opened and reapplied without visible damage, therefore deterring and preventing nefarious actors from interfering with the product
- Overt – visible to the eye and hard to copy, which deters from and ultimately prevents attempts to mimic the feature due to the high barrier to entry both from a cost and from a technical point of view
- Semi-overt – visible to the eye upon performing a simple action, which means the brand owner can choose when to change a feature from covert to overt by timing the invitation to the public to engage in the authentication of the product
- Covert/forensic – invisible to the eye, detectable using a hand-held device (covert) or laboratory equipment (forensic); being invisible, covert and forensic features do not prevent counterfeiting, but they facilitate unequivocal and quick in-field verification of authenticity and detection of counterfeits.
A combination of these features presents the most water-tight strategy against a number of illicit trade activities including counterfeiting, diversion, and infringement. To ensure successful implementation with minimal impact to current processes already in place, the most effective approach is to integrate the application of security features into existing processes within your manufacturing and vendor base, whether it is printing, labels, tamper evident seals or specialized overt and covert inks, using existing materials and packaging designs.
Going Digital: Connecting your Asset to the Cloud
Product marking is the foundation that supports digital security technologies, given that the physical form of digital identifiers can be validated when combined with robust printed security features.
Products become digital touchpoints by adding unique, item-level digital identifiers to the product or its packaging. Unique identifiers can be delivered in various formats such as overt or covert Datamatrix codes, QR codes, human readable alphanumeric codes, or embedded NFC chips, added to any part of the product or packaging or other carrier vehicle. These digital identifiers can also be embedded into an existing code format or added as a covert ‘twin’ of a visible code in cases where codes are at risk of being removed in an unauthorized attempt to destroy the traceability of the product.
In general, there are three main users of this technology:
- Supply Chain Participants – manufactures, distributors, 3rd party logistics
- Inspectors – a brand’s internal team, local law offices, law enforcement and customs agents
- Consumers/e\End-Users – for authentication verification and engagement
What’s Next: Using your Connected Asset to your Advantage
Connected products are typically used in three different ways and for different objectives. These include journey tracking, authentication and consumer engagement as shown in this graphic.
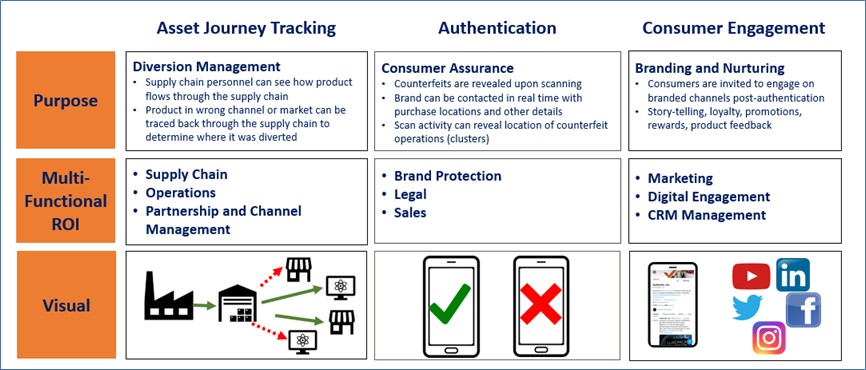
Driven by a rules engine that is calibrated by the brand owner or government, each of these paths direct critical data back to them in the form of actionable insights and analytics that are leveraged for strategic decisions across multiple agency focus areas or corporate functions, such as legal, operations, supply chain, marketing and others.
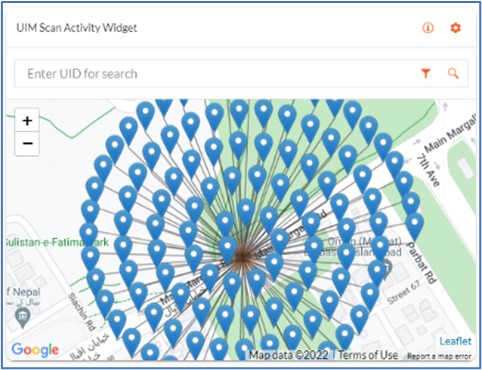
Examples of data that can be gleaned include locations of suspicious activity, excessive scan volume, geo- fence violations, multiple scans/single ID alerts, top scanned codes, and more.
The Role of Data: Collect, Analyze, Act, Share
There are many areas in which data can prove exceptionally meaningful. These include:
- Secure mark: validates if the product is genuine or fake
- Distribution: routes, port of entry, freight forwarders, dates, etc.
- Illicit activity: captures and ear-marks products/codes that are suspected as counterfeit or diverted
- Source: increasingly important raw materials and components
- Product: records product make or model, part number, batch and quality control data
- Production: captures manufacturer, date and time of production
- Location: identifies where was the product made, shipped, sold, or scanned
- Consumer: opt-in driven consumer intelligence, contact data, location of scan, device, engagement
This data can easily be shared across internal teams, with law enforcement and customs, and used for benchmarking and best practices in discussion with other brands.
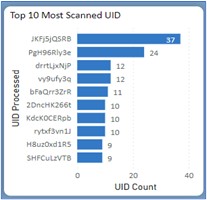
Examples of client dashboard in the Authentix DigiTrax™ platform
In summary, both physical and digital technologies play an important role in the fight against illicit trade. Creating digitally connected products turns them into valuable tools for inspection, reporting and communication. When leveraged to its full functionality, the combination of physical and digital technology is a game-changer for our industry.
To learn more about Authentix brand protection solutions, visit authentix.com.
