From Risk Identification to Full Implementation
Part 4 of The ABC’s of Brand Protection series by Authentix focusing on the global scope of the counterfeiting epidemic and how to act against it to protect your brand, your customers and your revenue.
 In articles 1, 2 and 3 of this series, we’ve discussed the vast scope of the global counterfeiting problem, the tactics used by counterfeiters, and security features used on many products today to detect and mitigate these compromises. You are aware that this is a massive problem but how do you determine if your products are at risk? Understanding and assessing these risks is the first vital step to start mapping out your company’s action plan, resulting in an effective brand protection program.
In articles 1, 2 and 3 of this series, we’ve discussed the vast scope of the global counterfeiting problem, the tactics used by counterfeiters, and security features used on many products today to detect and mitigate these compromises. You are aware that this is a massive problem but how do you determine if your products are at risk? Understanding and assessing these risks is the first vital step to start mapping out your company’s action plan, resulting in an effective brand protection program.
Five Steps to Determine if Your Products are at Risk
- Identify the risk areas
First, develop a risk inventory for your product line. The level of risk might differ depending upon supply chain complexity, geography, price point, margins, and anticipated demand. Consider these questions to identify vulnerabilities:
- Is my product line high volume with a low variable cost to produce?
- Are these products sold at higher price points and gross margins?
- Does my product line have an existing or potentially large market share?
- Does my product line and/or packaging currently have covert or overt security features that are economic deterrents to prevent counterfeiting?
- Do we sell through a complex supply chain and lose visibility to the point of sale?
- Are any of these products sold online or manufactured in countries without stringent counterfeit enforcement laws?
- Assess risk
Determine the likelihood, impact, and overall threat of each risk factor. How susceptible is each product in your portfolio for attempted compromise? Use this information to create a portfolio of the higher risk products which includes:
- Aggregated risks – score each product with weighted indicators to prioritize by risk potential
- Map of the supply chain environment – what are the highest points of exposure and where do we have access?
- Potential short- and long-term damage – Consider:
- How could adverse events of illicit supply affect consumer trust in your brand?
- What about liability from health issues caused by compromised product?
- How much market share and revenue dilution could be happening?
- Develop a risk management strategy
Examine the results of your risk assessment to create an integrated strategy for each high-risk product that includes potential solutions to address all the foreseen threats:
- Adopt a defined set of policies and procedures where your stakeholders are aligned
- Look at available solutions to address specific product risks by threat area; for example – consumer safety vs. losses from diversion activity
- Address what actionable steps can be taken at the physical points in the supply chain where threats are the greatest
- Play out each risk scenario and escalation possibilities for contingent action upon the event including communication strategies
- Prepare a budget to implement solutions based on your assessment
- Create an action plan
Responses to the most pressing threats can now be put into action by organizing management, information, and technology solution partner(s). Your action plan should include the following three categories:
- Detection and Deterrence – solutions that provide detection of a non-authorized product in the supply chain, proactive awareness campaigns, investigatory procedures upon detection, vendor agreements that include security policies for handling or manufacturing higher risk products, and unannounced audits of downstream distribution partners.
- Enforcement – the pre-determined action you plan to take upon the detection of an adverse event. This might depend on the event’s geography, supply chain level, and the resources you have allocated for enforcement.
- Prosecution – plan the specific steps that will be taken to support investigative and forensic efforts upon the discovery and confirmation of responsible parties. In some countries, enforcing your supply agreements against offending distribution partners might be a better course of action than criminal prosecution.
- Monitor risk and continually re-evaluate your strategy
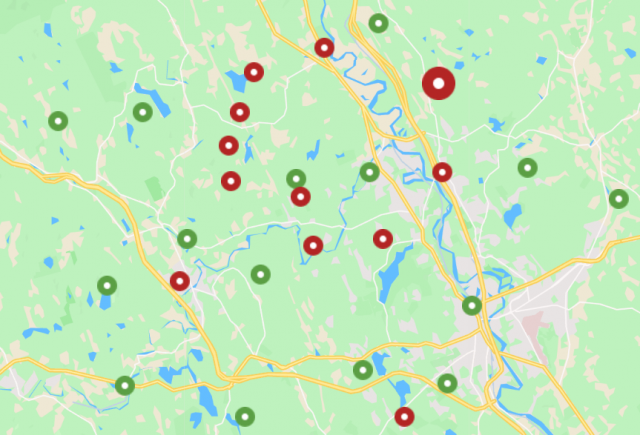
The last step in your strategy is a closed loop. Constant review of your data analytics offers an opportunity to better understand changing risks, increased or decreased vulnerabilities, and allows you to refine your actionable policy proactively. Today, data visualization coupled with a strong physical security element is even more critical in the fight against illicit product placement activity. Analyze and act on these insights revealed in the reporting information– from new counterfeit hot spots to changing risk as time evolves.
The fact is no one solution or security measure will be the panacea to address all instances of product compromise across the global marketplace. However, as a brand owner you can assess these risks and select the right security solution partner(s) to help minimize the damage and keep you in charge rather than being in a reactionary stance. Also, it is important to select solution partners with lengthy experience in multiple industries who can offer a full suite of technology and service solutions that can both be rapidly implemented and scale to your business needs.
For more brand protection basics – why it is necessary, how it works, who is vulnerable, how to implement an effective program, what to look for in a technology partner, and which emerging technologies will make a difference in the future – download the eBook, The ABC’s of Brand Protection.


 Covert or Semi-Covert Security Features – Covert and semi-covert features are invisible to the naked eye or disguised but can be found and measured with specialized handheld devices using proprietary optics and detection algorithms for rapid, secure field authentication.
Covert or Semi-Covert Security Features – Covert and semi-covert features are invisible to the naked eye or disguised but can be found and measured with specialized handheld devices using proprietary optics and detection algorithms for rapid, secure field authentication. One Tactic Is Not Enough
One Tactic Is Not Enough

 Organized criminal enterprises have developed sophisticated networks of willing players throughout the global supply chain in practically every industry to cause such destruction. Some of their tactics include:
Organized criminal enterprises have developed sophisticated networks of willing players throughout the global supply chain in practically every industry to cause such destruction. Some of their tactics include:




 The Oil and Gas industry is facing increasing pressure to take urgent actions toward a low-carbon future. Some have responded already by setting bold Net Zero and other ambitious Sustainability targets by 2050. With the current geopolitical landscape, the industry continues to be challenged to innovate in navigating climate and environmental issues driven by constantly changing policy and regulations.
The Oil and Gas industry is facing increasing pressure to take urgent actions toward a low-carbon future. Some have responded already by setting bold Net Zero and other ambitious Sustainability targets by 2050. With the current geopolitical landscape, the industry continues to be challenged to innovate in navigating climate and environmental issues driven by constantly changing policy and regulations.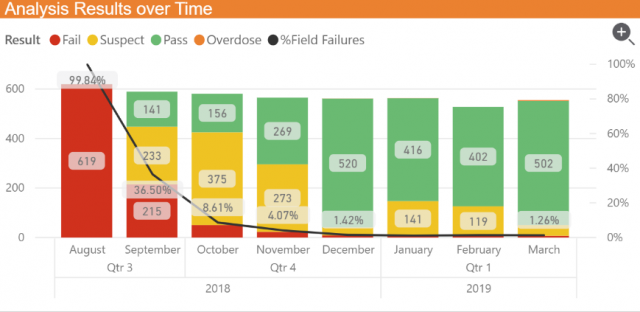

 In a
In a 
