By Mike Consterdine, Brand Account Development Manager
Globally, many companies have committed to the fight against plastic pollution, with manufacturers changing components and materials to produce more recyclable packaging. The time and investment put into this sustainability goal is also a balancing act with businesses becoming carbon neutral.
However, a sometimes forgotten consideration is that counterfeit products entering the supply chain may lack sustainable materials and are often unsafe and non-compliant. In this light, an essential component of sustainability efforts is to prevent counterfeiting.
The main motivation for those conducting illicit trade is financial gain. Therefore, there is an overwhelming argument that sustainability is not considered in the manufacturing, distribution and sale of counterfeit products. Counterfeiters manufacture these goods in factories that are often unregulated and include cheaply sourced and substandard materials that are not only harmful to workers but also contribute to the pollution of the environment.
So the question is, can companies truly achieve sustainability while at the same time not considering or having a plan to remediate counterfeit goods? We’ll see that sustainability and counterfeiting prevention go hand-in-hand.
The Impact of Counterfeiting
While it’s well-known that counterfeiting and intellectual property infringement supports organized crime, there are also other societal impacts to consider:
- Illicit trade rings traffic people across borders for exploitative labor, often in abhorrent conditions with little or no compensation.
- Across multiple sectors, including apparel, consumer goods, cosmetics, electronics and pharmaceuticals, counterfeit products have been proven to contain hazardous and toxic elements. When those products come into contact with a person or are consumed, they can be harmful or even fatal.
- Counterfeit or non-compliant products may find their way into legitimate manufacturing and distribution channels, compromising supply chain integrity. This results in companies being unable to prove that the product or process adheres to company sustainability statements and practices.
- When counterfeit products are seized, there is an opportunity to reuse or recycle them. However, de-labeling a branded item is not always possible as this process can also be costly, and some product materials are unsafe to reuse. In these circumstances, the products will be destroyed by court order, impacting the environment with further waste and pollution.
The ability to prevent counterfeiting substantially reduces all these risks.
How to Prevent Counterfeiting
There are many ways companies can prevent counterfeiting. First, they should conduct a comprehensive review of intellectual property rights and supply chain channels. This process will provide insight into the strengths and weaknesses of company processes and their IP portfolio. The results allow efficient and effective decision-making by legal, regulatory and enforcement teams and support sales, marketing and operational divisions.
The next essential step, even if the company has an in-house brand protection specialist, is collaborating with key partners. These partners can include regional enforcement teams, online brand protection service providers and those who are experts in securing products through authentication and traceability solutions.

An online brand protection company can assess the market while providing an overall view of the extent of the IP infringement problem, whether that be in counterfeit, design or copyrights. Engaging a third-party provider for brand protection services assists in time management. They also can conduct online takedowns and provide actionable intelligence for prioritizing offline targets.
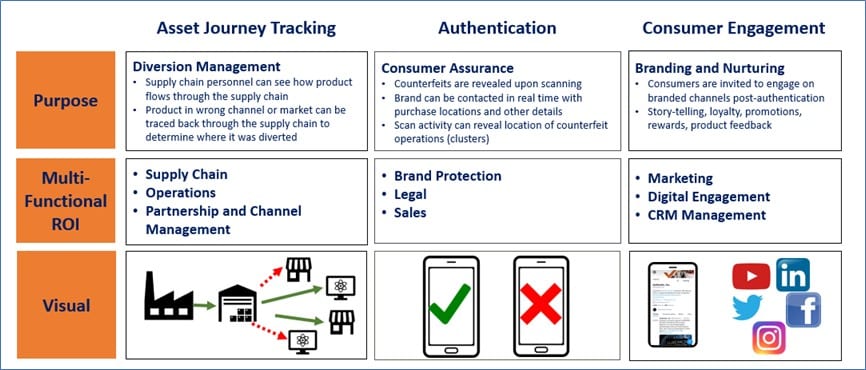
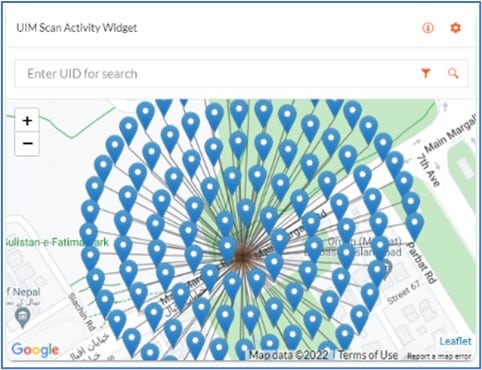
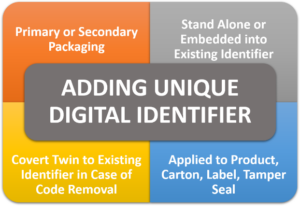
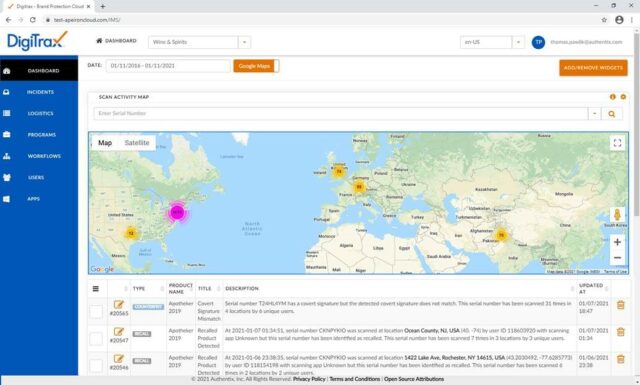
By applying a unique and secure identifier to a product or packaging, a product can be authenticated or tracked through its lifecycle, with all data on the product stored in a cloud-based platform for various business functions. Consumers or field investigators also can immediately authenticate a product by scanning the identifier via an app, a forensic reader or a mobile/cellular device.
By implementing these strategies, a company can mitigate its risk of counterfeiting, diversion and non-compliant products entering the legitimate supply chain.
Return on Investment
Brand protection can be seen as a cost center. But a return on investment can be determined by increased consumer confidence through fewer customer returns, higher sales driven by the removal of infringing online content and offline target prioritization. Brand protection can also help avoid costly product recalls, which will likely increase emissions, representing another link between preventing counterfeits and sustainability.
Implementing secure brand protection technologies can also lead to more efficient processes and less waste, supporting company sustainability initiatives.
Combining Sustainability and Counterfeiting Prevention
While counterfeiting can be deemed a byproduct of a successful business, it can irreparably damage a brand’s reputation with customers and the general public. It also invites questions regarding what the intellectual property rights holder is doing to prevent unregulated, often harmful, illegal practices.
Corporate social responsibility is often seen as a buzzword. But, when it comes to consumer trust and sustainability statements, it is imperative to consider all factors. Reviewing component sourcing, manufacturing processes, policies and regulations is only the start to increasing sustainability.
Brand protection, online and offline, is more than “stopping the fakes.” It’s also about protecting reputation, human life and the environment.
Ready to Learn More?
Trust Your Brand Protection to Authentix
As the authority in authentication solutions, Authentix brings enhanced visibility and traceability to today’s complex global supply chains. For over 25 years, Authentix has provided our clients with physical and software-enabled solutions to detect, mitigate and prevent counterfeiting and other illicit trading activity for currency, excise taxable goods, and branded consumer products. Brand protection is an integral component of our services.
Through our proven client partnership model and sector expertise, we offer custom solution design, rapid implementation, consumer engagement and complete program management to ensure product safety, protect revenue and maintain consumer trust and loyalty for the best global brands on the market. Contact us now to see what we can do for your brand.
Mike Consterdine, Account Development Manager for Brand, Authentix
Mike Consterdine has been involved in the Brand Protection industry for nearly 15 years, helping brands secure their products through protection and enforcement of their IP portfolio. Having worked as an external investigator for a number of global luxury and apparel brands, Mike also developed and managed the international enforcement program for a leading consumer electrical appliance manufacturer.
Using his wealth of knowledge in the field he is able to consult brand owners on best practices in anti-counterfeiting and anti-diversion programs. Representing Authentix, Mike will be able to outline how secure product marking enables authentication and traceability, whilst online to offline brand protection enables business growth.
Mike explains that Brand Protection is “a passion as well as a profession, protecting people is the reason. Whether you have counterfeiting, diversion or fraud issues, it’s key to be proactive and collaborate with your network to be successful in any Brand Protection program.”
To learn more about our brand protection solutions and how we can help you, please email Mike at Mike.consterdine@authentix.com.







 To expand its capabilities in digital brand protection for brand owners, Authentix has recently acquired Strategic IP Information Pte Ltd (SIPI), a leading online brand and content rights protection service.
To expand its capabilities in digital brand protection for brand owners, Authentix has recently acquired Strategic IP Information Pte Ltd (SIPI), a leading online brand and content rights protection service.