Protecting consumers and safeguarding your company’s brand identity and reputation is becoming increasingly challenging in today’s environment with the continued growth of counterfeit and diverted products entering the market. At the same time, consumers are taking a more proactive role in choosing to buy brands they know and trust, while expecting increased transparency in brand promise.
As supply chains become increasingly complex, brand owners are facing intense pressure to respond to traceability and transparency challenges by utilizing digital systems for collecting valuable data and analyzing and acting upon the visible trends to help consumers authenticate products at points of sale, or alternatively connect and engage with the brand owner directly via the web or app. A digital solution helps with monitoring product movement in the supply chain, as well as direct consumer feedback, to confirm legitimate or potential suspect product in the marketplace.
67% of consumers say brand trust has a great deal of influence over their buying decisions.
In todays connected marketplace, most companies already collect and use various forms of data analytics to drive ongoing business decisions and strategic initiatives. In fact, business action and decision making has become reliant on the use of data analytics to manage many day-to-day operations. Despite this growing reliance on data, most organizations have yet to apply the practice successfully when it comes to brand security. This can partly be attributed to the lack of reliable data available since the early adoption of digital track and trace capabilities for risk-based products is only beginning. The key to effectively using data in brand protection programs is to understand what data is available now, what data is needed that is not available, how to efficiently collect and analyze the data and lastly, what action can be taken based on this analysis to effectively reduce counterfeiting and diversion while simultaneously engaging directly with the consumer.
Data Identification
An enormous amount of meaningful data can be gleaned in digital tracking for brand protection programs including information about a product’s provenance, its journey through the supply chain, the location/date/time of associated transactions including consumer scan events, validation of authentication or suspected illicit activity, and even direct consumer marketing and engagement.
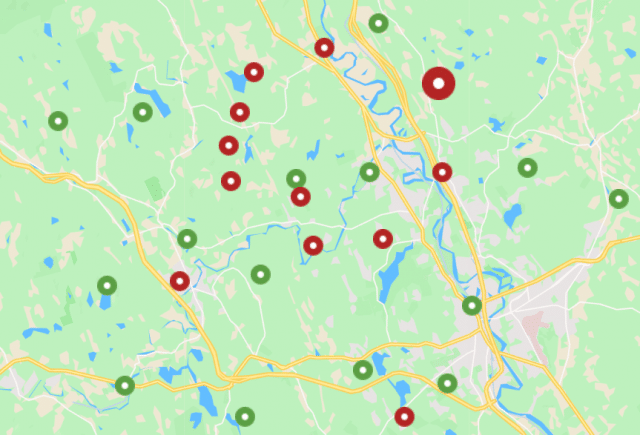
However, how to apply the data once collected can be different for each company. At Authentix, we collect supply chain and consumer interaction data from multiple sources and aggregate it into our secure cloud-based platform on behalf of our brand owner clients. From there we are able to configure rules and analyze data trends to provide our clients with complete visibility into the suspect events or grouped metadata revealing weak links or threats in supply chain operations that often point to product compromise.
Data Collection
The following are key areas for collecting data using digital track and trace technology.
- Data Carrier Technology – includes multiple formats of barcodes, NFC and RFID technologies for supply chain tracking, purchase and post purchase consumer engagement, inventory movement, and theft prevention. These technologies vary greatly in terms of volume capacity, costs, application requirements and security levels, so it is important to evaluate the best types of code formats and integration to existing manufacturing and packaging processes that best meet the minimum needs that would produce a valuable return.
- Track & Trace – can be accomplished during sourcing, manufacturing, distribution, and pre- and post-sale stages. During the printing, manufacturing or packaging process for example, the scope of implementation choices widen and we can provide multiple routes to enable tracking of product origin information, manufacturing location(s), production lines designation and more. Additionally, as the product nears closer to the point of sale, we’ll begin seeing authentication activity and the collection of meaningful data such as distributor and consumer interaction and engagement, and sustainability and circularity.
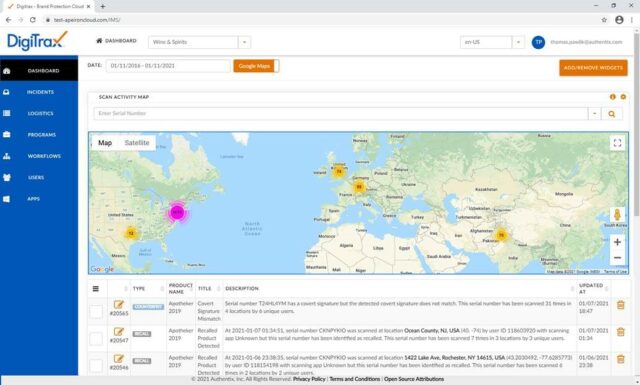
- Authentication – in most digital track and trace systems, analysis of authenticity is often achieved via a smartphone. This can be by company inspectors using a proprietary mobile application all the way to the consumer who can interact with the product without having to download a mobile app. Using the Authentix DigiTrax™ track and trace solution as an example of direct consumer engagement, the smartphone user simply scans a proprietary and encrypted QR code which directs them to a custom URL experience that can include, among other things, the unique information associated with the individual product scanned. These consumer product scan events including geo location, date, time, product and product provenance information are submitted to the secure cloud-based DigiTrax platform where the information can be used to understand purchasing trends, market directly to the user, or allow the user to authenticate the product using proprietary codes or PINs. If designed for the purpose, the results of the authentication can be sent back to the user in real time. This technology also enables inspectors in the field and other key stakeholders to identify the authenticity of a product instantly using a more sophisticated mobile application. In addition, consumers may also use the DigiTrax platform to verify authenticity of other products or for the purpose of continuing engagement with brand owner purely for marketing purposes.
- Online Surveillance and Enforcement – are methods, systems, and services used to identify, investigate and takedown unauthorized e-commerce websites that deal in illicit trade of counterfeit, diverted, or stolen products. This is accomplished through automated online tools and services such as marketplace monitoring, WeChat micro tasking, and machine learning which can identify risk levels, hot zones and image matching to police and eliminate unauthorized sales of product and illegal use of trademarks on the internet.
Putting Data to Use
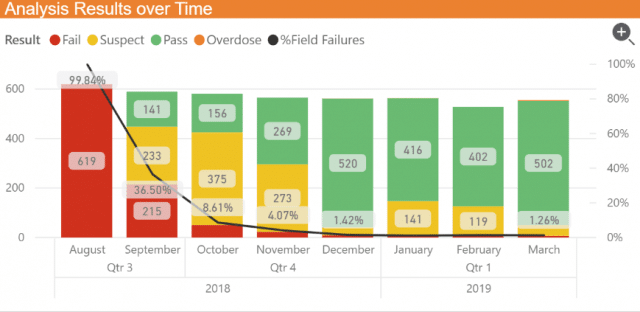
Reliable and timely data feedback enables brand owners to quickly answer complex supply chain events, pinpoint trouble spots, and take corrective and even preventative action to reduce the instances and threats of unauthorized product entering the marketplace. Data can be used to assess multiple business-centric operations to increase sales and market share, acquire and build trust with new customers, and reinforce brand assurance, to name a few. In addition, as consumers become more reliant on smartphones for collecting and communicating information, brand owners can capture consumer data to tailor experiences and increase engagement and loyalty.
Using Data to Drive Success
Authentix customers are using valuable brand protection data and analytics in multiple ways with great success. In one customer success story, an international wine exporter faced counterfeiting and diversion issues in China, resulting in loss of consumer trust and risk to its strong market share and long term brand loyalty it had spent years building. Authentix helped the client implement a multi-layered digital authentication solution with covert and overt on-product features that flags, collects and analyzes all inspector and consumer scanning activity including the capability of retail product authentication by the consumer. The result? Over 150 counterfeit retail locations were identified and remediated. Also, through direct consumer engagement, loyal brand purchasers became more confident in product authenticity and the client was able to maintain premium pricing for their superior and quality products.
In another example, an international brand customer incurred online marketplace counterfeiting in Asia, putting consumer health, safety and loyalty at risk as well as decreasing revenues. Authentix helped the client implement a multi-phased online brand protection monitoring solution and services to identify and investigate the online sale of spurious product and locate complicit bottling and closure manufacturers involved in the illicit trading. Website takedowns were initiated, resulting a 90% reduction in fake products in Indonesia, 1,500 online listing takedowns in Malaysia, and 13 raids and enforcement actions conducted in China.
Start Big or Small. Just Start.
It’s important to point out that you do not have to implement a full scale approach to digital authentication initially and it’s easy to begin collecting and leveraging data – even if it’s just one product or product line for a particular geography. Alternatively, digital automation for brand protection programs can be implemented in a sweeping fashion as an end-to-end solution from the start with a full technology suite. Most clients choose to implement in logical steps based on risk assessment, ease of implementation, and to the most critical geographic areas. The key is to get a secure digital mark on your product and start the data collection process. Ultimately, it is how much data, the association of the data elements for analysis, and the conclusions and action you take that determines how much your brand protection program can be enhanced by bringing in digital track and trace automation. The key is to start, analyze, adjust, expand and continue until the data flow and insights provided are resulting in the development and refinement of actions and policies to take command of the risks faced each day.
Learn more about Authentix brand protection solutions, HERE.


 To expand its capabilities in digital brand protection for brand owners, Authentix has recently acquired Strategic IP Information Pte Ltd (SIPI), a leading online brand and content rights protection service.
To expand its capabilities in digital brand protection for brand owners, Authentix has recently acquired Strategic IP Information Pte Ltd (SIPI), a leading online brand and content rights protection service.
 Authentix is pleased to be included in the June/July edition of
Authentix is pleased to be included in the June/July edition of  In articles
In articles 
 Covert or Semi-Covert Security Features – Covert and semi-covert features are invisible to the naked eye or disguised but can be found and measured with specialized handheld devices using proprietary optics and detection algorithms for rapid, secure field authentication.
Covert or Semi-Covert Security Features – Covert and semi-covert features are invisible to the naked eye or disguised but can be found and measured with specialized handheld devices using proprietary optics and detection algorithms for rapid, secure field authentication. One Tactic Is Not Enough
One Tactic Is Not Enough

 Organized criminal enterprises have developed sophisticated networks of willing players throughout the global supply chain in practically every industry to cause such destruction. Some of their tactics include:
Organized criminal enterprises have developed sophisticated networks of willing players throughout the global supply chain in practically every industry to cause such destruction. Some of their tactics include:




 The Oil and Gas industry is facing increasing pressure to take urgent actions toward a low-carbon future. Some have responded already by setting bold Net Zero and other ambitious Sustainability targets by 2050. With the current geopolitical landscape, the industry continues to be challenged to innovate in navigating climate and environmental issues driven by constantly changing policy and regulations.
The Oil and Gas industry is facing increasing pressure to take urgent actions toward a low-carbon future. Some have responded already by setting bold Net Zero and other ambitious Sustainability targets by 2050. With the current geopolitical landscape, the industry continues to be challenged to innovate in navigating climate and environmental issues driven by constantly changing policy and regulations.